Source: AWS
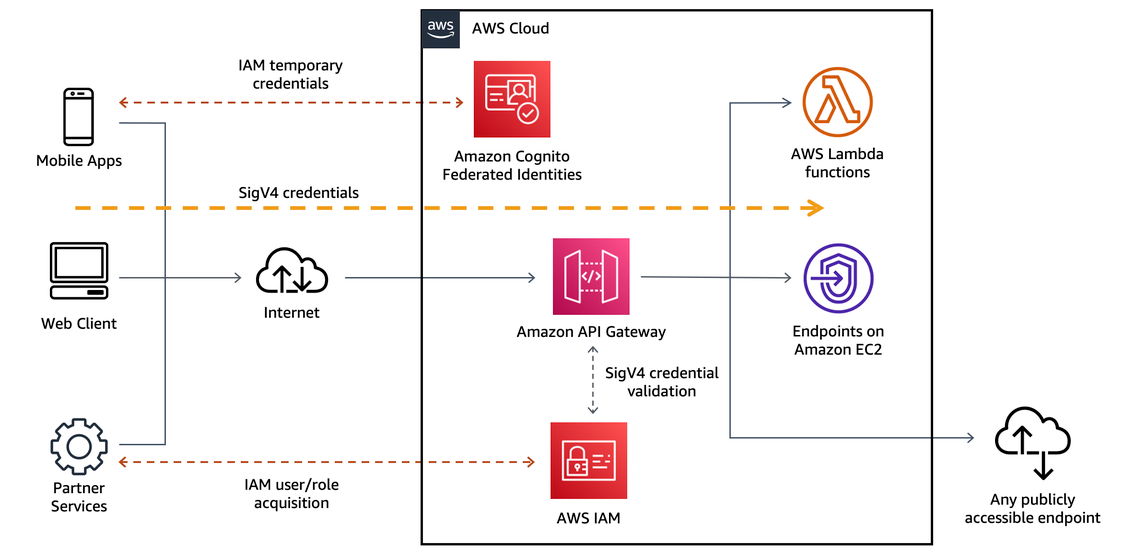
Imagine in a project you are using Amazon API Gateway to define REST APIs. You, as a developer want to allow only IAM users from another AWS account to access the APIs. What would you do?
- Create an IAM Permission Policy
Create an IAM policy in the other AWS account (the account where the IAM users are located) that grants the necessary permissions to invoke the API Gateway methods.
The policy should look something like this:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "execute-api:Invoke",
"Resource": "arn:aws:execute-api:{region}:{account-id}:{api-id}/*"
}
]
}
- Attach the Policy to the IAM Users or Groups
Attach the created IAM policy to the IAM users or groups in the other AWS account who need access to the API.
- Set the Method Authorization Type for the APIs to AWS_IAM:
In the AWS account where the API Gateway is deployed, set the authorization type for the API methods to AWS_IAM. This can be done via the API Gateway console, AWS CLI, or AWS SDKs.
4.1. Create a Resource Policy for the APIs to Allow Access for All IAM Users from the Other AWS Account
Create a resource policy for the API Gateway to allow access for all IAM users from the other AWS account. This policy is attached directly to the API Gateway. An example resource policy might look like this:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::{other-account-id}:root"
},
"Action": "execute-api:Invoke",
"Resource": "arn:aws:execute-api:{region}:{account-id}:{api-id}/*"
}
]
}
The Principal field specifies the IAM user or role that is allowed to invoke the API. In here "root" means all IAM users in the other account.
4.2. Create a Resource Policy for the APIs to Allow Access for Each IAM User Only Alternatively, you can create a resource policy for the API Gateway to explicitly allow each IAM user from the other AWS account to access the APIs. This policy is attached directly to the API Gateway. An example resource policy might look like this:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::{other-account-id}:user/{iam-username}"
},
"Action": "execute-api:Invoke",
"Resource": "arn:aws:execute-api:{region}:{account-id}:{api-id}/*"
}
]
}
The Principal field specifies the IAM user or role that is allowed to invoke the API. In here, you can specify the IAM user's ARN to allow access only for that user, which is more granular.
Source
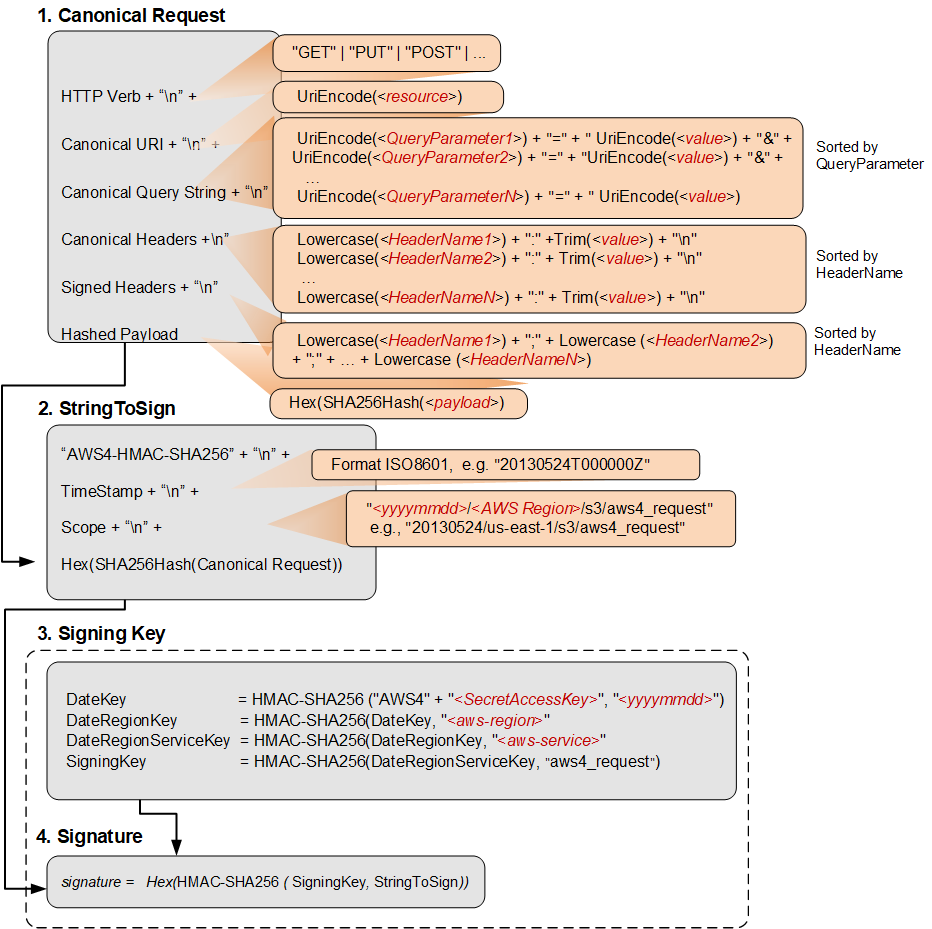
- Use Signature Version 4 to Sign the API Requests:
Ensure that the API requests are signed using AWS Signature Version 4. This involves using the AWS SDKs or manually signing the requests following the steps outlined in the AWS documentation.
If you are using the AWS SDKs, the SDK will handle the signing process for you. But if you are making requests manually, you should follow the steps mentioned in the Create a signed AWS API request user guide or the AWS Signature Version 4 for API requests.
Further Reading
For more information on securing your APIs with Amazon API Gateway, check out these resources:
