Source: AWS
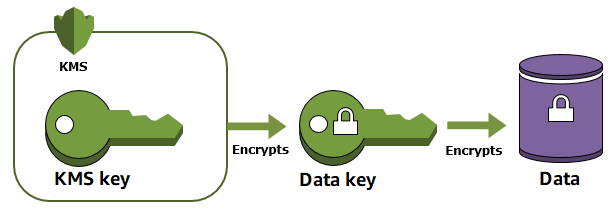
Envelope encryption in AWS Key Management Service (KMS) enhances data security and efficiency by encrypting plaintext data with a data key, which is then encrypted with another key, often a root key. This method ensures robust protection by securing the data keys and allows for efficient re-encryption of keys rather than large datasets.
Benefits of Envelope Encryption
- Enhanced Security: Encrypted data keys can be securely stored.
- Operational Efficiency: Re-encryption of data keys is less resource-intensive.
- Strength of Cryptographic Algorithms: Combines the speed of symmetric keys with the management ease of public keys.
Encryption Context
The encryption context in AWS KMS adds non-secret key-value pairs to cryptographic operations. It acts as additional authenticated data (AAD), ensuring that encrypted data is tied to specific context, which must be provided exactly during decryption.
- Purpose: Used for data integrity and additional security.
- Usage: Required for decryption if used during encryption; must be an exact match.
- Examples:
📌 To describe data: {"department": "10103.0"}
📌 In Amazon EBS: {"aws:ebs:id": "vol-abcde12345abc1234"}
Access Control and Auditing
Encryption contexts assist in auditing by appearing in AWS CloudTrail logs, providing a clear trail of cryptographic operations. Policies and grants can leverage encryption contexts for fine-grained access control.
Key Policy and Grants
Key Policy:
Defines permissions for managing and using KMS keys.
Grants:
Allow specific actions for AWS principals, ideal for temporary permissions.
They can include constraints like EncryptionContextEquals, ensuring tight control over data access.
Practical Example
A key policy for controlling decryption access might look like:
{ "Effect": "Allow", "Principal": {"AWS": "arn:aws:iam::111122223333:role/RoleForExampleApp"}, "Action": "kms:Decrypt", "Resource": "*", "Condition": {"StringEquals": {"kms:EncryptionContext:AppName": "ExampleApp"}} }
A grant request example:
aws kms create-grant --key-id 1234abcd-12ab-34cd-56ef-1234567890ab --grantee-principal arn:aws:iam::111122223333:user/exampleUser --operations GenerateDataKey --constraints EncryptionContextEquals={Purpose=Test}
Important Details and Best Practices
1. Non-Secret Nature of Encryption Context:
The encryption context is not encrypted and is logged in plaintext in AWS CloudTrail logs. It should not contain sensitive information. Instead, it should describe the data being encrypted or decrypted.
2. String Literal Requirement:
Keys and values in the encryption context must be simple literal strings. Using other types like integers or floats will result in AWS KMS interpreting them as strings.
Unicode characters are allowed, but characters not permitted in key or IAM policies cannot be used in policy condition keys.
3. Primary Use for Integrity and Access Control:
The encryption context verifies the integrity and authenticity of cryptographic operations. It can also control access to symmetric encryption AWS KMS keys in key policies and IAM policies.
Use kms:EncryptionContext: and kms:EncryptionContextKeys condition keys to enforce permissions based on specific encryption context keys or key-value pairs.
4. Grant Constraints:
AWS KMS supports two grant constraints involving the encryption context: EncryptionContextEquals and EncryptionContextSubset.
Permissions in the grant are effective only when the encryption context in the request meets the requirements of the grant constraints.
5. Example of Grant Constraint:
aws kms create-grant --key-id 1234abcd-12ab-34cd-56ef-1234567890ab --grantee-principal arn:aws:iam::111122223333:user/exampleUser --retiring-principal arn:aws:iam::111122223333:role/adminRole --operations GenerateDataKey --constraints EncryptionContextEquals={Purpose=Test}
A matching request:
aws kms generate-data-key --key-id 1234abcd-12ab-34cd-56ef-1234567890ab --key-spec AES_256 --encryption-context Purpose=Test
6. Logging and Best Practices:
AWS KMS uses AWS CloudTrail to log the encryption context, showing which KMS keys were used to encrypt or decrypt data. Ensure that sensitive information is not included in the encryption context.
Store enough of the encryption context to recreate it when needed, enhancing the security and integrity of encrypted data.
Conclusion
AWS KMS envelope encryption provides a robust, efficient method for managing data security, combining the strengths of symmetric and asymmetric encryption. By leveraging encryption contexts and fine-grained policies, organizations can ensure secure and efficient cryptographic operations.
For more details, visit the AWS KMS documentation on envelope encryption.
